From 3 6 0 websites guards Openssl effort loophole online testing platform wangzhan. Several recommended practices are available for reading or download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies. We recommend that you check the other servers that you manage. This option is still under development and only exists in the Google Code repository. This means that there is no way to tell if your information was stolen previously from a site or a service that has now fixed it. OpenSSL's heartbeat processing logic does not detect a heartbeat packet in the length field and subsequent data fields are consistent, the attacker can take advantage of this, structural abnormalities of the data packet, to obtain the heartbeat data where the memory area of the subsequent data. 
| Uploader: | JoJojind |
| Date Added: | 4 December 2005 |
| File Size: | 33.18 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 51326 |
| Price: | Free* [*Free Regsitration Required] |
Use of these names, logos, and brands does not imply endorsement.
The criteria are as follows: An attacker can retrieve sensitive information by using the stated vulnerability in the following scenarios: However, a warning will be displayed in the output to notify the user that SSLv2 ciphers will not be detected. Additionally, virtual servers that do not use SSL profiles and pass SSL traffic to the back-end web servers will not protect the back-end resource servers.
For information about changing user passwords, refer to the following documentation: For more information about using iRules to protect the back-end servers, refer to the Supplemental Information section.
The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
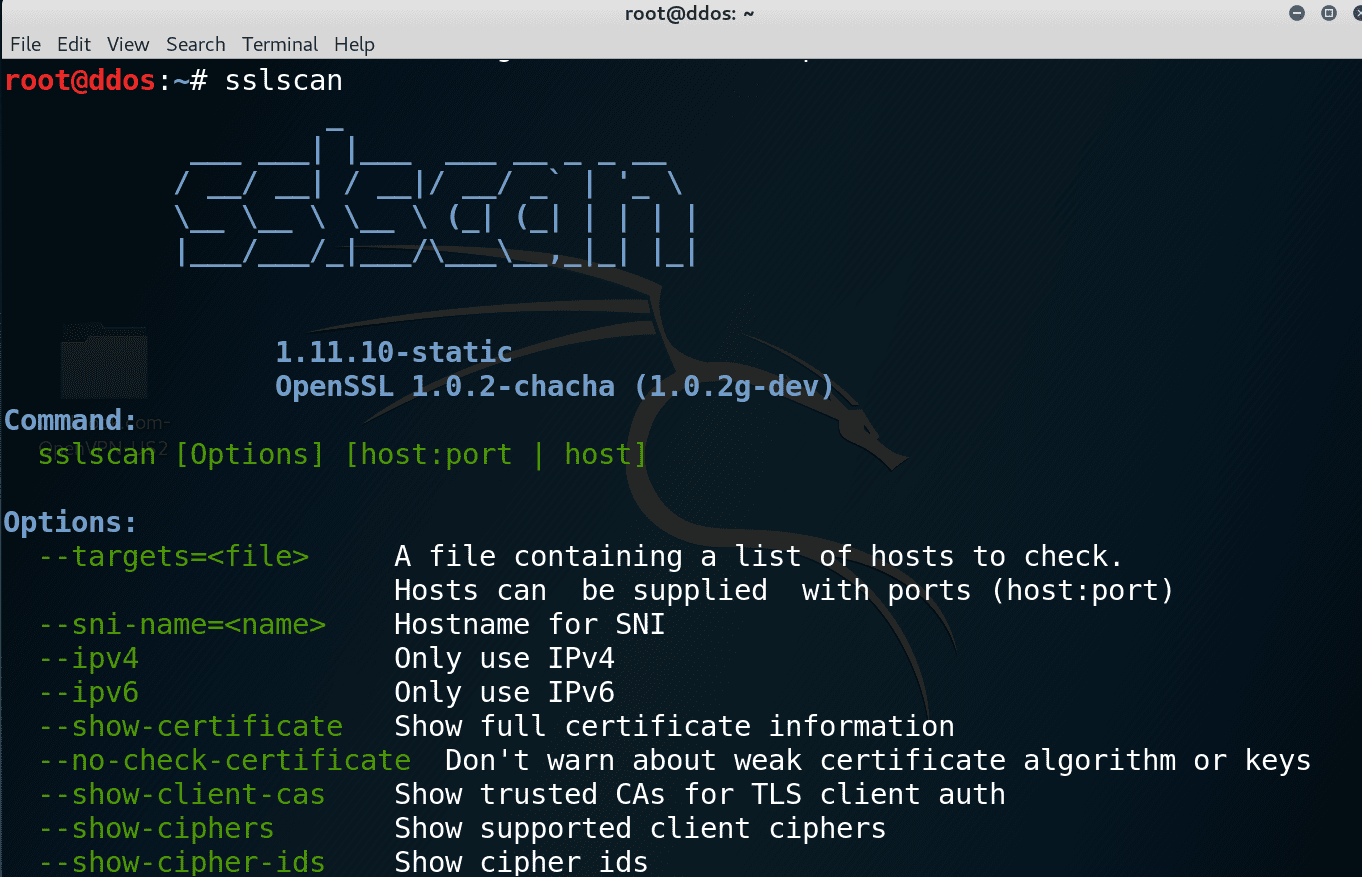
sslscan v releases: tests SSL/TLS enabled services to discover supported cipher suites
Schneider Electric provides automation and information technologies and systems. Log in to the Configuration utility. Codenomicon released a web application that will scan small firmware updates or applications to determine if a vulnerable version of OpenSSL is used.

In case you want to test a particular protocol version SSLv2, SSLv3 and TLSv1 are currently supported instead of all the protocols you can use the --ssl2--ssl3 or --tls1 option respectively. Therefore, Schneider Electric Wonderware has issued a patch and a security bulletin addressing this vulnerability in all versions. All product names, logos, and brands are property of their respective owners. There is two machine-readable bnary that you can use:.
sslscan Download – Detect SSL Versions & Cipher Suites (Including TLS)
This is due in part sslscann ICS terminology and sslsxan terms that have become widely available because of an increasing public body of knowledge with detailed ICS information.
Furthermore, even though each heartbeat only allows requests to have a data size limited to 64 kB segments, it is possible to send repeated requests to retrieve more 64 kB segments, which could include encryption keys used for certificates, passwords, usernames, and even sensitive content that were stored at the time.
As such, the Windows version should be considered experimental. If for whatever reason you can't install this package, follow the instructions above for statically building against OpenSSL. Any system that may have exposed this vulnerability should regenerate any sensitive information secret keys, passwords, etc.
sslscan - tests SSL/TLS enabled services to discover supported cipher suites
So based on the queries of Internet users, we answered some frequently asked questions about the bug. Below is list of the affected components: The following DevCentral article contains additional information hinary using iRules to assist in mitigating this vulnerability when terminating TLS traffic on back-end servers. Troubleshooting ConfigSync and device service clustering issues Schneider Electric Wonderware has produced a patch that mitigates this vulnerability.
Human-readable format is not that good for software to parse. Extract the random data for computation of keys.
Analysis Report sslscan.exe
This document also contains a list of vendors, products, and product versions that has evaluated their products and have asserted that their products are not affected by the OpenSSL vulnerability.
Changes are as follows: Advanced usage Specifying protocol versions to test In case you want to test a particular protocol version SSLv2, SSLv3 and TLSv1 are currently supported instead of all the protocols you can use the --ssl2--ssl3 or --tls1 option respectively. Changing system maintenance account passwords But, in order to protect your online accounts you should at least change your passwords immediately for the sites that resolved the issue and for the sites not affected by the bug as well, just to make sure that you are safe.
The Bluebox Heartbleed Scanner looks for apps installed on your device that have bundled their own version of OpenSSL and the scanner also checks the version of the library and whether heartbeat is enabled or not.
We continue to monitor the product advisories of our major vendors for any potential issues. Nevertheless, to ensure there is no additional risk, we strongly encourage you to request a new password.

No comments:
Post a Comment